
YARA Rules: Unveil Hidden Threats Your Antivirus Can’t See
The Hidden Power of YARA Rules in Today’s Threat Landscape
In today’s increasingly sophisticated cyber threat landscape, security professionals are turning to YARA rules as the “Swiss Army knife” of threat hunting.
When sophisticated malware slips through commercial security tools, YARA rules offer the precision and flexibility that traditional signature-based detection simply cannot match.
YARA rules have transformed how threat hunters identify and classify malicious code in the wild. Whether investigating suspicious files, hunting specific malware families, or building automated detection systems, YARA provides capabilities that pre-packaged security solutions lack.
This guide provides practical insights into creating, optimizing, and implementing YARA rules across different platforms to enhance your malware detection capabilities.
Essential YARA Resources for Malware Hunters
Before diving deeper into YARA rules for malware detection, bookmark these fundamental resources:
- Official YARA Repository: github.com/VirusTotal/yara – Download the latest version and access official documentation.
- Yara-Rules: github.com/Yara-Rules/rules – An extensive collection of ready-to-use YARA rules maintained by the community.
- Signature-Base: github.com/Neo23x0/signature-base – High-quality YARA signatures maintained by renowned security researcher Florian Roth.
- Awesome-YARA: github.com/InQuest/awesome-yara – A curated list of YARA-related resources, tools, and libraries.
Understanding YARA rule: The Ultimate Malware Detection Tool
Created by Victor Manuel Alvarez while at VirusTotal, YARA allows security professionals to create detailed descriptions of malware families based on textual or binary patterns. Unlike traditional antivirus signatures that rely on simple hash values, YARA rules for malware detection can be as simple or sophisticated as needed.
Here’s what a basic YARA rule looks like:
rule suspicious_powershell_execution {
meta:
author = "Security Analyst"
description = "Detects suspicious PowerShell execution with encoded commands"
severity = "High"
date = "2023-03-15"
strings:
$encoded_cmd = "-enc" nocase
$bypass = "bypass" nocase
$hidden = "-w hidden" nocase
condition:
$encoded_cmd and ($bypass or $hidden)
}Explanation: This rule is structured to detect PowerShell commands that may be attempting to hide malicious activity. The syntax uses string variables prefixed with $ to define patterns to search for. The nocase modifier makes the search case-insensitive, which is crucial because attackers often vary capitalization to evade detection. The condition uses logical operators (and, or) to specify that the file must contain the encoded command parameter AND either the bypass or hidden window parameter – a combination commonly used in malicious PowerShell scripts.
The Anatomy of Effective YARA Rules for Malware Detection and Implementation
Creating effective YARA rules requires understanding their basic structure. Let’s break down the essential components:
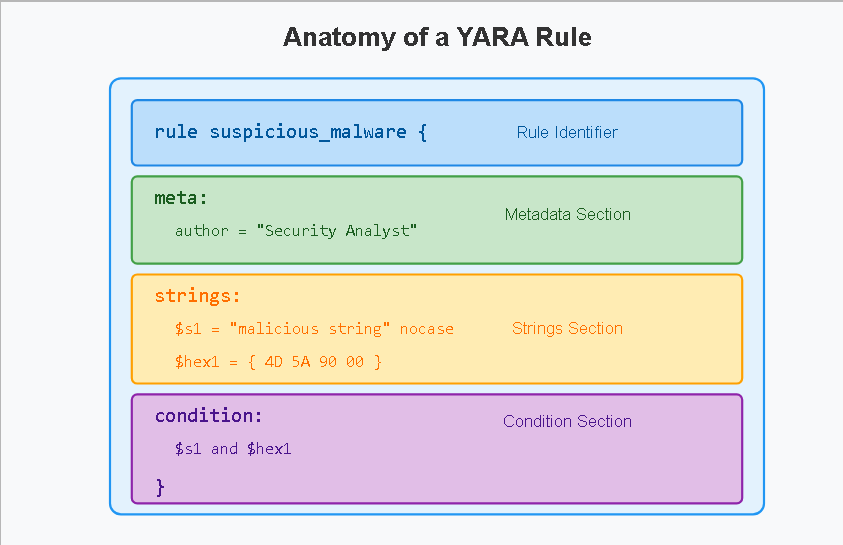
Rule Identification
Every YARA rule starts with a unique name that describes what it’s detecting:
rule emotet_document_macro {
// Rule content goes here
}Follow a naming convention that includes the malware family or technique followed by the specific artifact you’re targeting for easier management of rule collections.
Metadata Section
While metadata doesn’t affect functionality, it’s crucial for documentation:
meta:
author = "Your Name"
description = "Detects Emotet malware in Office documents with macros"
reference = "https://example.com/emotet-analysis"
hash = "abcdef123456789..."
severity = "Critical"
date = "2023-03-15"Explanation: The metadata section uses key-value pairs to document important information about the rule. This doesn’t affect detection but provides crucial context for other analysts. The reference and hash fields help validate the rule against known samples, while the severity field helps prioritize alerts when matches are found.
Strings Section
This is where you define the patterns for malware detection:
strings:
// Text strings (case sensitive)
$s1 = "PowerShell.exe"
// Text strings (case insensitive)
$s2 = "rundll32" nocase
// Hex strings
$hex1 = { 4D 5A 90 00 03 00 00 00 }
// Regular expressions
$re1 = /password=[^&]*/
// Wide (Unicode) strings
$w1 = "malicious" wideExplanation: This strings section demonstrates the versatility of YARA pattern matching. Plain text strings like $s1 match exact character sequences, while hex strings like $hex1 match binary patterns (here, the MZ header found in PE files). The regular expression $re1 uses a more flexible pattern matching approach to detect passwords in URL parameters, and the wide modifier on $w1 enables detecting Unicode strings, which is crucial for finding malware that uses Unicode to hide text patterns.
Condition Section
The condition section defines logical relationships between patterns:
condition:
// Simple AND condition
$s1 and $s2
// OR condition
any of ($s1, $s2, $hex1)
// Counting occurrences
#s1 > 3
// Positional checks
$s1 at 0 and $hex1 in (0..1024)
// File type restriction
uint16(0) == 0x5A4D and all of them
// Complex nested logic
($s1 and $s2) or ($hex1 and $re1)Explanation: The condition section uses Boolean logic to determine when a rule should trigger. The any of construct provides flexibility by matching if any listed pattern is found, while #s1 > 3 counts occurrences to detect repeated patterns. Positional operators like at and in verify where patterns appear, which is useful for finding specific file structures. The uint16(0) == 0x5A4D checks for the MZ header to ensure the file is a Windows executable before applying other conditions, reducing false positives.
Real-World YARA Rules for Malware Detection That Get Results
Let’s explore practical YARA rules that have solved specific security challenges:
Example 1: Detecting Suspicious Document Macros
Office documents with malicious macros remain a common attack vector. Here’s a YARA rule that consistently detects them:
rule suspicious_office_macro {
meta:
description = "Detects suspicious patterns in Office document macros"
author = "Security Analyst"
severity = "Medium"
strings:
$auto_open = "AutoOpen" nocase
$document_open = "Document_Open" nocase
$create_object = "CreateObject" nocase
$shell = "Shell" nocase
$powershell = "powershell" nocase
$hidden = "-w hidden" nocase
$encoded = "-enc" nocase
condition:
uint32(0) == 0xE011CFD0 and // Office document magic bytes
($auto_open or $document_open) and
$create_object and
($shell or $powershell) and
($hidden or $encoded)
}Explanation: This rule targets malicious Office macros by combining several key indicators. The uint32(0) == 0xE011CFD0 checks the file signature to confirm it’s an Office document before proceeding. The strings section looks for auto-execution mechanisms (AutoOpen, Document_Open) and suspicious operations like creating shell objects and running hidden PowerShell commands. The condition requires multiple suspicious elements to be present together, reducing false positives while maintaining high detection rates for actual malicious macros.
Example 2: Identifying Potential Ransomware
Ransomware often exhibits specific behavioral patterns. This YARA rule looks for those indicators:
rule potential_ransomware {
meta:
description = "Detects potential ransomware based on common behaviors"
author = "Security Analyst"
severity = "High"
strings:
$encrypt_func = {68 ?? ?? ?? ?? 68 ?? ?? ?? ?? E8 ?? ?? ?? ?? 83 C4 08}
$ransom_note1 = "YOUR FILES HAVE BEEN ENCRYPTED" nocase
$ransom_note2 = "SEND BITCOIN TO" nocase
$file_enum = "FindFirstFileW"
$file_enum2 = "FindNextFileW"
condition:
uint16(0) == 0x5A4D and // PE file
filesize < 5MB and
($encrypt_func and $file_enum and $file_enum2) or
(any of ($ransom_note*) and any of ($file_enum, $file_enum2))
}Explanation: This rule uses a multi-layered approach to detect ransomware. The hex pattern $encrypt_func uses wildcards (??) to match common encryption function signatures while allowing for variable addresses. The condition combines file type verification (uint16(0) == 0x5A4D), size restriction to reduce scanning overhead, and logical combinations of technical indicators (encryption functions and file enumeration APIs) with contextual indicators (ransom note text). The wildcards in the hex string allow flexibility to match variants of the same function while maintaining specificity.
Example 3: Detecting Fileless Malware in Memory
Some of the most sophisticated malware operates entirely in memory. This YARA rule has successfully detected such threats:
rule fileless_powershell_backdoor {
meta:
description = "Detects fileless PowerShell backdoor patterns in memory"
author = "Security Analyst"
severity = "Critical"
strings:
$net_webclient = "Net.WebClient" nocase
$download_string = "DownloadString" nocase
$invoke_expression = "IEX" nocase
$hidden_window = "-WindowStyle Hidden" nocase
$encoded_cmd = /[A-Za-z0-9+/]{50,}={0,2}/ // Base64 pattern
condition:
($net_webclient and $download_string) and
($invoke_expression or $hidden_window) and
$encoded_cmd
}Explanation: This rule targets fileless malware by focusing on PowerShell memory artifacts. The regular expression $encoded_cmd = /[A-Za-z0-9+/]{50,}={0,2}/ is specifically crafted to match Base64-encoded commands, which are commonly used to obfuscate malicious payloads. The pattern requires at least 50 Base64 characters followed by 0-2 equals signs (typical Base64 padding). The condition combines indicators of network downloading with code execution and encoding to precisely identify fileless backdoors while minimizing false positives.
Optimizing YARA Rules for Malware Detection: Lessons from False Positives
Early in my YARA journey, I created a rule to detect a specific ransomware variant that ended up matching hundreds of legitimate files. This experience taught me valuable lessons about optimization.
Balancing Specificity and Coverage
The most important YARA skill is finding the right balance between specific rules (which might miss variants) and broad rules (which generate false positives). Follow these principles:
- Start specific, then broaden: Begin with highly specific patterns and carefully expand the rule
- Test against clean datasets: Always validate rules against known-good files
- Layer multiple conditions: Use multiple pattern requirements to reduce false positives
- Include file type restrictions: Limit rules to relevant file types when possible
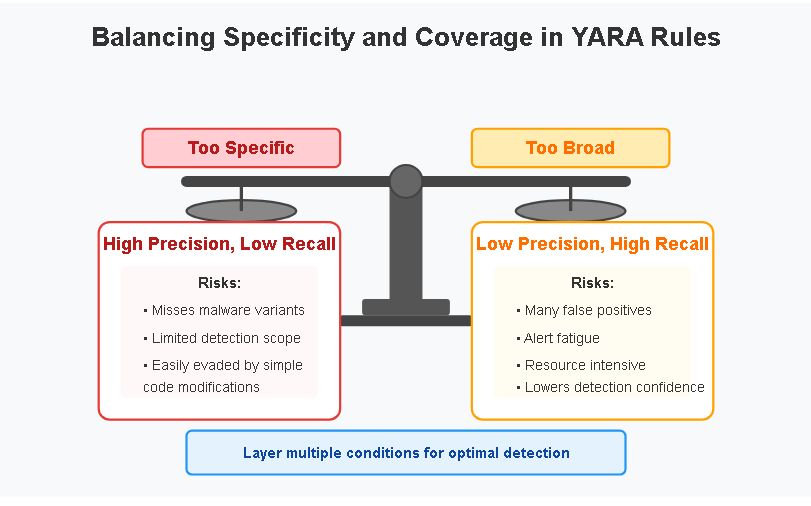
Here’s an improved rule that balances specificity and coverage:
rule improved_ransomware_detection {
meta:
description = "Balanced rule for ransomware detection with reduced false positives"
version = "2.0"
strings:
$encrypt_func = {68 ?? ?? ?? ?? 68 ?? ?? ?? ?? E8 ?? ?? ?? ?? 83 C4 08}
$ransom_note1 = "YOUR FILES HAVE BEEN ENCRYPTED" nocase
$ransom_note2 = "SEND BITCOIN TO" nocase
$file_enum = "FindFirstFileW"
$file_enum2 = "FindNextFileW"
$benign_program = "Microsoft.SQLServer.Management.Sdk" // Known false positive
condition:
uint16(0) == 0x5A4D and // PE file
filesize < 5MB and
not $benign_program and
(
($encrypt_func and $file_enum and $file_enum2) or
(any of ($ransom_note*) and any of ($file_enum, $file_enum2))
)
}Explanation: This optimized rule demonstrates false positive reduction strategies. The not $benign_program condition explicitly excludes a known legitimate program that was triggering false positives. The nested condition structure requires multiple indicators to be present together, increasing confidence in detections. The rule maintains its detection capabilities by offering two different detection paths (either technical indicators of encryption plus file enumeration OR ransom text plus file enumeration), providing flexibility while maintaining specificity.
Performance Considerations for YARA Malware Detection
Poorly optimized YARA rules can consume excessive resources. Use these optimization techniques:
- Put the fastest conditions first: Start with file size or magic byte checks before complex string matching
- Limit wildcard usage: Excessive wildcards in hex patterns dramatically slow scanning
- Be cautious with regex: Complex regular expressions can cause performance issues
- Use named strings efficiently: Reuse named strings instead of defining the same pattern multiple times
Implementing YARA Rules Across Different Operating Systems
One of the greatest strengths of YARA for malware detection is its cross-platform compatibility across Windows, Linux, and macOS environments.
YARA on Windows
Setting up and running YARA on Windows is straightforward:
- Installation:
- Download the latest YARA release from the official GitHub repository
- Extract the files to a location like
C:Program Filesyara - Add the YARA directory to your system PATH to run it from any command prompt
- Basic Scanning:
# Scan a single file yara64.exe rules.yar suspicious_file.exe # Scan a directory recursively yara64.exe -r rules.yar C:UsersusernameDownloads # Output only matching rules yara64.exe -m rules.yar suspicious_file.exe - Automating Scans with PowerShell:
# PowerShell script to scan specific directories and log results $yaraPath = "C:Program Filesyarayara64.exe" $rulesPath = "C:securityrulesmalware_rules.yar" $scanPaths = @("C:Users", "D:shared") $logFile = "C:securitylogsyara_scan_$(Get-Date -Format 'yyyy-MM-dd').log" foreach ($path in $scanPaths) { Write-Host "Scanning $path..." & $yaraPath -r $rulesPath $path | Out-File -Append $logFile }
YARA on Linux
Linux provides a powerful environment for YARA malware detection:
- Installation:
# Debian/Ubuntu sudo apt-get install yara # CentOS/RHEL sudo yum install epel-release sudo yum install yara - Basic Scanning:
# Scan a file yara rules.yar /path/to/suspicious_file # Scan a directory recursively yara -r rules.yar /var/www/ # Process scan results with grep yara -r rules.yar /var/www/ | grep "malware_family" - Automation with Cron:This bash script provides thorough system scanning:
#!/bin/bash # Configuration YARA_RULES="/etc/yara/rules.yar" LOG_FILE="/var/log/yara_scan_$(date +%Y%m%d).log" CRITICAL_DIRS=("/home" "/var/www" "/tmp" "/opt") # Create log header echo "YARA Scan Started: $(date)" > $LOG_FILE echo "System: $(hostname)" >> $LOG_FILE echo "----------------------------------------" >> $LOG_FILE # Perform scan for dir in "${CRITICAL_DIRS[@]}"; do echo "Scanning $dir..." >> $LOG_FILE yara -r $YARA_RULES $dir >> $LOG_FILE 2>&1 done # Check for matches if grep -q "malicious_" $LOG_FILE; then echo "ALERT: Malicious content detected!" | mail -s "YARA Alert on $(hostname)" security@example.com fi echo "Scan Completed: $(date)" >> $LOG_FILE
YARA on macOS
Setting up YARA on macOS for malware detection:
- Installation:
# Using Homebrew brew install yara - Basic Scanning:
# The syntax is identical to Linux yara rules.yar /path/to/file # Scanning Applications directory yara -r rules.yar /Applications/
Integrating YARA with Your Security Toolkit
YARA’s true potential is realized when integrated with other security tools for comprehensive malware detection:
YARA + Memory Forensics
Some sophisticated malware never touches the disk. By combining YARA with memory forensics frameworks, you can detect these evasive threats:
# Scan a memory dump for YARA matches
volatility -f memory.dmp --profile=Win10x64 yarascan -y /path/to/rules.yarExplanation: This command demonstrates integrating YARA with Volatility, a popular memory forensics framework. The --profile=Win10x64 parameter specifies the operating system profile to use when analyzing the memory dump, which is crucial for correctly interpreting memory structures. The yarascan plugin applies YARA rules directly to memory regions, enabling detection of malware that exists only in RAM.
Building a Comprehensive YARA Rule Library for Malware Detection
A structured approach to maintaining effective YARA rules includes:
- Categorize rules by threat type: Organize rules into categories like ransomware, backdoors, exploit kits, etc.
- Implement version control: Store rules in a Git repository to track changes and facilitate collaboration
- Add expiration dates where appropriate: Some rules targeting specific campaigns may become irrelevant over time
- Document false positive handling: Include comments about known false positives and how to address them
- Regular testing and validation: Periodically test rules against known-good files to check for false positives
A well-organized folder structure might look like:
/yara-rules
/malware-families
/ransomware
emotet.yar
ryuk.yar
/backdoors
cobaltstrike.yar
/techniques
code_injection.yar
evasion_techniques.yar
/file-types
office_macros.yar
suspicious_scripts.yar
/tools
testing_framework.py
rule_validator.pyConclusion: The Evolution of YARA in Modern Threat Detection
YARA rules remain essential for effective threat hunting, with YARA-X now representing the next generation of this technology. YARA-X delivers significant advantages including faster processing of complex patterns, better error reporting, an enhanced CLI, and a modular design for better developer tools.
While YARA-X currently lacks some features of traditional YARA (include statements, process scanning, and API compatibility), its performance improvements with complex regular expressions and extensive loops—up to 5-6x faster in some cases—make it worth considering for many security teams.
The broader YARA ecosystem continues to evolve with memory scanning capabilities, machine learning integration, YARA-L for log analysis, and growing community collaboration platforms.
Whether you choose YARA or YARA-X, start with simple rules and build gradually. Both technologies offer substantial returns in improved security posture and threat detection capabilities.
For a detailed comparison between YARA and YARA-X, visit the official documentation at: https://virustotal.github.io/yara-x/docs/intro/yara-x-vs-yara/
What has been your experience with YARA or YARA-X? Have you tested YARA-X’s performance improvements? Share your insights in the comments below.



Leave a Reply