Stop Unwanted Traffic NOW – Use this Free Linux GeoIP Block List
Introduction
Hey everyone! Running a Linux server open to the internet often feels like dealing with a constant barrage of unwanted attention – scans, probes, and login attempts from all over. A highly effective way to mitigate this is by implementing a free Linux GeoIP block, essentially telling your server to ignore traffic from entire countries you don’t serve. If you’re looking for a robust, cost-free method that works for both IPv4 and IPv6 and integrates well with UFW (Uncomplicated Firewall), especially on Debian-based systems (like Debian or Ubuntu), then combining UFW with IPset is a fantastic solution.
This guide provides a step-by-step walkthrough for setting up this powerful duo on your server. We’ll cover installation using apt, configuring UFW and IPset, creating an auto-updating script for free country IP lists, ensuring persistence, and crucially, how to implement three different flexible geoblocking strategies to perfectly match your security needs. Let’s build that digital moat and achieve a more secure server with this free Linux GeoIP block technique.
Why Granular Geoblocking is Powerful
Basic geoblocking is useful, but having flexible control allows you to tailor your security precisely, especially on a versatile platform like Debian. You might need your website (ports 80/443) to be globally accessible, while restricting administrative access (like SSH) only to specific, trusted countries. Or perhaps you only need to protect a single custom service port. This free Linux GeoIP block method using UFW and IPset provides that necessary granularity, letting you decide exactly which traffic gets checked against your allowed country list. It’s a smart way to enhance security without impacting legitimate global users where needed.
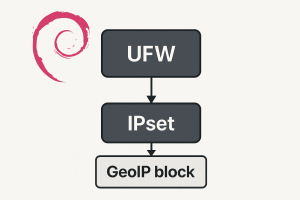
Core Tools: UFW & IPset for Your Free Linux GeoIP Block on Debian
Our setup relies on these key components, readily available on Debian:
- UFW: The user-friendly firewall interface manages
iptables(IPv4) andip6tables(IPv6). We’ll use its configuration files to inject our custom rules. - IPset: Essential for efficiently handling the potentially massive lists of IP addresses associated with entire countries. It allows the firewall to perform checks very quickly.
ipset-persistent: The service that makes our lives easier by automatically saving and restoringipsetdata across server reboots, ensuring our free Linux GeoIP block stays active.- Free IP Lists: Sources like ipdeny.com provide the raw data (IP ranges per country) needed to populate our ipsets.
Step 1: Installation (UFW, IPset and Persistence)
First, on your Debian/Ubuntu system, let’s install the necessary packages using apt:
sudo apt update
sudo apt install ufw ipset ipset-persistent -yThis installs the firewall frontend, the ipset utility, and the service needed to automatically save and restore our sets across reboots.
Step 2: Basic UFW Configuration (Dual-Stack Ready)
Configure UFW with sensible defaults. Crucially, allow essential services like SSH before enabling the firewall, and ensure IPv6 support is turned on (usually default on modern Debian).
# Set secure default policies
sudo ufw default deny incoming
sudo ufw default allow outgoing
# --- ALLOW SSH (Critical!) --- Change port if needed
sudo ufw allow ssh
# --- ALLOW Web Traffic (Needed for Strategy A & C) ---
sudo ufw allow http # Port 80
sudo ufw allow https # Port 443
# --- Allow other ports you want managed by standard UFW rules ---
# Example: sudo ufw allow 2266/tcp
# --- Verify/Enable IPv6 in UFW ---
# Check /etc/default/ufw and ensure IPV6=yes
sudo nano /etc/default/ufw
# Make sure this line is present and set to yes:
# IPV6=yes
# Save if changed.
# --- Enable UFW --- (Confirm with 'y')
sudo ufw enable
# --- Check Status ---
sudo ufw status verboseStep 3: Creating the Allowed Country IPsets (v4 & v6)
Create the ipsets that will hold our allowed country IP ranges:
# Create IPv4 set
sudo ipset create allowed_countries hash:net -exist
# Create IPv6 set
sudo ipset create allowed_countries_v6 hash:net family inet6 -existStep 4: The Dual-Stack IP Update Script
This script handles fetching IPv4 and IPv6 lists from ipdeny.com and updating the ipsets. Save it as /usr/local/sbin/update_geoip_set.sh. Modify the COUNTRIES array with the codes for countries you want to ALLOW.




Leave a Reply