
SMS Security Risks: Why It’s Important Abandoning SMS for Both Messaging and 2FA (And Why You Should Too)
The Shocking Truth About Your Text Messages
Have you ever stopped to consider who might be reading your text messages? I hadn’t given it much thought until recently, when I fell down a digital privacy rabbit hole that completely changed my perspective on communication security. What I discovered about traditional SMS (Short Message Service) was alarming enough to make me permanently switch to more secure alternatives. The SMS security risks, for both regular messaging and two-factor authentication (2FA), are far more serious than most people realize.
Most people don’t realize how exposed their everyday text messages truly are. We’ve been using this technology for over three decades (SMS recently celebrated its 30th anniversary), yet it remains essentially unchanged and seriously flawed from a privacy standpoint.
I remember when SMS revolutionized how we connected. Those 160-character messages changed everything in personal communication. But just because something is ubiquitous doesn’t mean it’s optimal, and I’ve learned that there are compelling reasons to move beyond this outdated technology.
The Fundamental Security Flaws of SMS and Their Architecture
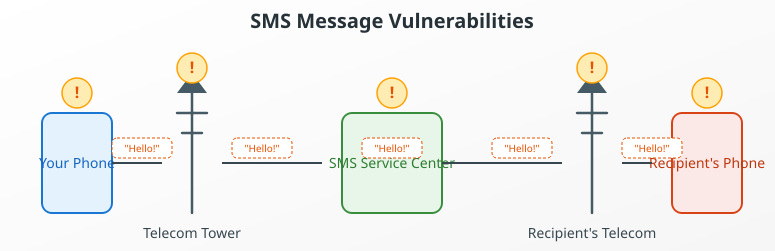
When I send an SMS, I used to imagine it traveling directly from my phone to my friend’s device. The reality is much less secure. Traditional text messages function through a “store and forward” mechanism, where the message first goes to a central service center operated by your telecom provider before being routed to the recipient.
To fully understand the scope of the problem, it’s crucial to examine the underlying architecture and SMS security risks:
The SMS infrastructure is based on the SS7 (Signaling System No. 7) protocol, developed in the 1970s, when security was not a design priority. Unfortunately, this outdated protocol has fundamental flaws because:
- It does not implement a rigorous authentication model between network nodes
- It lacks a granular authorization system for signaling operations
- It operates with a model of implicit trust between network operators
SMS messages traverse this infrastructure following a complex path:
- The mobile device transmits the message through the SDCCH (Stand-alone Dedicated Control Channel) control channel
- The BTS (Base Transceiver Station) receives and forwards it to the MSC (Mobile Switching Center)
- The MSC sends the message to the operator’s SMSC (Short Message Service Center)
- The SMSC temporarily stores the message and schedules delivery
- When the recipient is available, the SMSC routes the message through the SS7 network
- The message is delivered to the recipient’s device via its local MSC and BTS
This process creates several serious SMS security risks:
1. Zero Encryption Protection (and its weaknesses)
The most alarming aspect I discovered is that SMS messages are transmitted completely unencrypted. In practice, this means your messages are like postcards passing through the postal system: anyone handling them along the way can read their contents.
SMS Message Flow
And even the little encryption present is weak:
Weak Encryption Only in the Radio Segment: Encryption is limited to the radio segment (between the device and the BTS) and uses obsolete algorithms:
- A5/1: Developed in the 1980s, it uses 64-bit keys but is vulnerable. Since 2010, TMTO (Time-Memory Trade-Off) attacks can decrypt it in seconds with precomputed tables (rainbow tables) of about 2TB.
- A5/2: A deliberately weakened version of A5/1, decryptable in real-time.
- A5/3 (KASUMI): More robust, but not universally implemented and with documented vulnerabilities.
Lack of Perfect Forward Secrecy: SMS does not implement it. If an attacker obtains the keys, they can decrypt all intercepted historical messages.
At any point in this chain, your message is in plain text and could be viewed by:
- Employees of your telecom provider
- Government agencies with legal access
- Hackers who breach telecom systems
- Anyone who gains physical access to your unlocked phone
I find this lack of encryption particularly concerning when sending sensitive information.
2. Your Messages Are Stored (For How Long?)
Another uncomfortable truth about SMS security risks is that telecom providers don’t just transmit your messages, they store them. Retention policies vary, but in many cases, messages could be stored for months or even years.
This storage creates multiple privacy concerns:
- Operators can analyze message content for marketing purposes
- Message history could be subpoenaed in legal proceedings
- Data breaches could expose years of personal communications
- Aggregated message data can be sold to third parties
Many operators have privacy policies that explicitly allow them to analyze and monetize customer data, including SMS.
3. The Critical Security Risks of SMS for Two-Factor Authentication
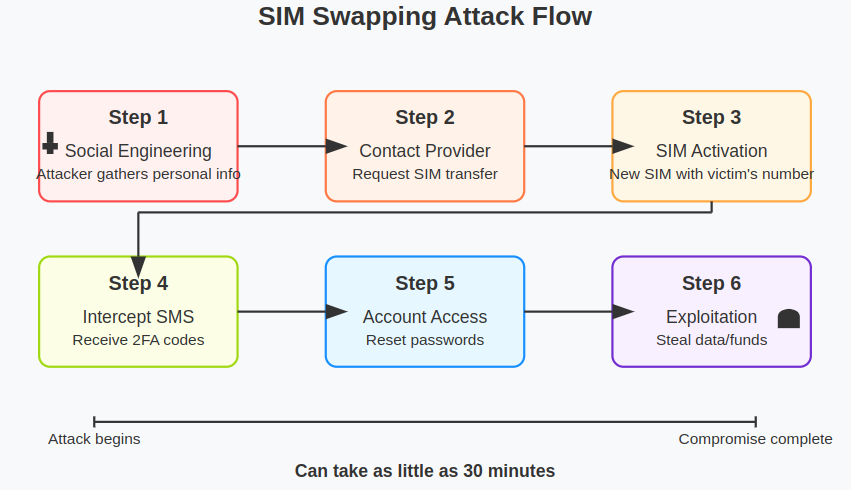
One of the most pernicious SMS security risks is the vulnerability of SMS to SIM swapping attacks. This occurs when someone convinces your carrier to transfer your phone number to a new SIM card they control, effectively hijacking your identity.
Once an attacker controls your number, they can:
- Receive all your incoming SMS messages
- Bypass SMS-based two-factor authentication
- Reset passwords for email, banking, and social media accounts
- Access sensitive accounts that use phone verification
I’ve heard numerous horror stories of people losing access to cryptocurrency wallets, email accounts, and banking services due to SIM swapping attacks. The financial and personal damage can be devastating.
SIM swapping Attak Flow
Why Your Phone Number Is a Privacy Liability
Have you considered how long you’ve had your current phone number? For most of us, it’s years or even decades. This persistence creates a significant privacy problem, and it’s one of the major SMS security risks.
Your phone number has likely become a permanent digital identifier linked to:
- Your legal identity (required for phone registration in many countries)
- Countless online accounts and services
- Your physical location (via cell tower triangulation)
- Your social and professional contacts
Unlike passwords or usernames, changing your phone number is socially and logistically difficult. This permanence makes it an ideal tracking mechanism.
Phone numbers were never designed with privacy in mind, yet they’ve become one of our primary digital identifiers. This fundamental design flaw cannot be corrected without switching to completely different communication systems.
The Financial Cost of SMS You Might Be Ignoring
While many mobile plans now include unlimited SMS, this isn’t universal. In fact, across many regions of the world, SMS messages still have per-message fees that can quickly accumulate. Moreover, when traveling internationally, where roaming charges for SMS can be surprisingly high.
Even with “unlimited” plans, there’s usually a hidden cost in terms of data collection and privacy sacrifices. Your “free” messages are effectively paid for through the commercial exploitation of your communication data and metadata.
The Superior Alternatives I’ve Embraced
After discovering these SMS security risks, I began exploring more secure messaging options. What I found was remarkable: not only do modern messaging applications offer significantly better security, but they also provide enhanced features that make SMS feel like a relic of another era.
Encrypted messaging apps offer substantial protection against the vulnerabilities inherent in SMS.
End-to-End Encryption: The Gold Standard
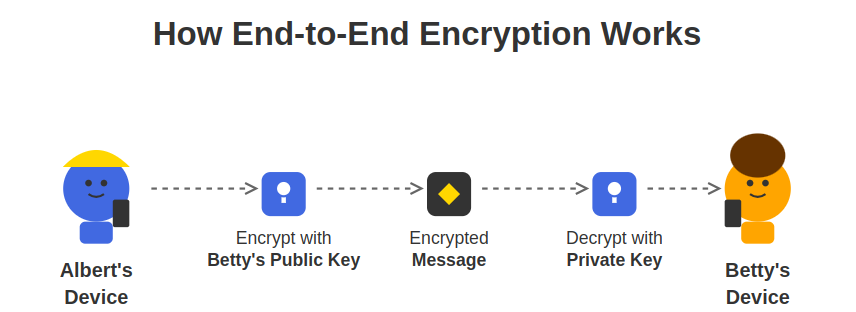
The most important security feature I look for in any messaging app is end-to-end encryption (E2EE). This technology encrypts messages directly on your device, ensuring that only you and the intended recipient can read them.
how e2ee works
With proper E2EE, not even the company operating the messaging service can read your communications. This represents a fundamental security improvement over SMS. E2EE alternatives implement advanced asymmetric encryption, often with elliptic curves and perfect forward secrecy.
Signal: My Primary Recommendation
After testing numerous secure messaging apps, Signal has become my primary recommendation for most users. It offers:
- Strong, audited end-to-end encryption by default
- A familiar interface that resembles standard messaging apps
- Open-source code that security experts can verify
- Optional disappearing messages for sensitive conversations
- Minimal metadata collection compared to alternatives
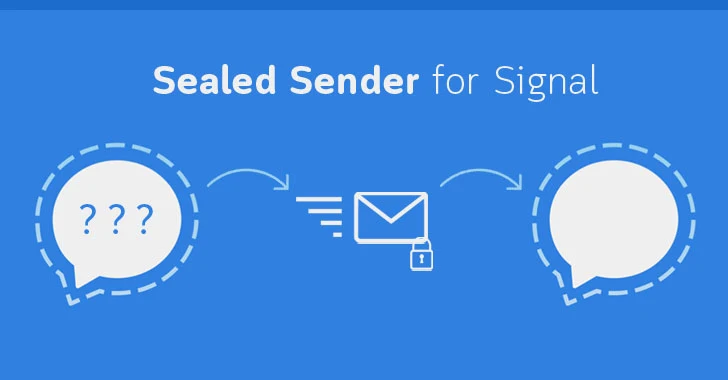
I particularly appreciate Signal’s “Sealed Sender” feature, which hides who is messaging whom even from Signal’s servers. This additional layer of privacy protection addresses metadata concerns that many other secure apps overlook.
sealed sender signal
A significant technical advantage of Signal is precisely the implementation of “Sealed Sender”:
- The sender creates an encrypted message for the recipient
- This message is encapsulated in an external envelope
- The envelope contains only the recipient’s identity and a cryptographic certification
- Signal’s server can authenticate the sender without knowing their identity
- Sender-recipient correlation metadata is never available in plain text
The Signal Protocol in Detail
The Signal protocol, also used by WhatsApp, implements:
- Elliptic curves X25519 for Diffie-Hellman key exchange
- Perfect Forward Secrecy with periodic key renegotiation
- Triple Diffie-Hellman (3-DH) for authentication
- Double Ratchet Algorithm for key derivation
- HMAC-SHA256 for message integrity
- AES-256 in CBC mode for encryption
This system ensures that even if an attacker compromises a session key, they can decrypt only a single message, not the entire conversation.
For Advanced Privacy: Identifier-Free Messaging
For situations requiring extraordinary privacy, I’ve explored messaging platforms that eliminate permanent identifiers entirely. These systems use temporary, rotating addresses instead of static identifiers like phone numbers or usernames.
This approach prevents even the service provider from building a complete picture of your communication patterns over time. Although these solutions require greater technical sophistication, they represent the cutting edge of truly private digital communication.
RCS: A Partial Solution to Understand
Rich Communication Services (RCS) represents the mobile industry’s attempt to modernize SMS. While it offers improvements like better media sharing and typing indicators, its security benefits remain limited and inconsistent.
Some RCS implementations offer encryption, but this varies based on:
- Device manufacturer
- Mobile carrier
- Messaging app used
- Whether both parties support compatible encryption standards
In my testing, I’ve found that RCS encryption works reliably between certain Android devices using Google Messages, but interoperability with other platforms remains problematic. While RCS represents progress, it does not yet provide the consistent security of dedicated encrypted messaging apps.
The Social Challenge: Converting Your Contacts
The biggest hurdle I’ve faced in switching away from SMS isn’t technical—it’s social. Secure messaging apps only work if your contacts also use them. I’ve developed several strategies to encourage friends and family to switch:
- Start with the closest contacts and gradually expand
- Explain the SMS security risks in simple, relatable terms
- Help with installation and initial setup
- Use group chats to create social pressure for adoption
- Be patient and maintain SMS as a fallback during the transition
Focusing on positive features (better photo sharing, richer messaging options) often works better than emphasizing security concerns alone. Most people care about privacy in theory but are motivated by improved user experience in practice.
Real-World Breach Examples That Changed My Perspective
Several major security incidents reinforced my decision to abandon SMS. In 2023, several major telecom providers experienced security breaches that exposed customer data, including SMS content and metadata. These incidents affected millions of users and demonstrated the inherent vulnerability of centralized messaging systems.
The 2022 SALT Typhoon hack particularly highlighted these vulnerabilities. As documented by cybersecurity researchers, this sophisticated actor targeted telecom providers and compromised SMS communications on a large scale. The attack demonstrated how nation-state-level actors could exploit fundamental weaknesses in traditional telecommunications infrastructures to conduct widespread surveillance.
One particularly alarming case involved hackers exploiting telecom network vulnerabilities to intercept SMS authentication codes, leading to widespread account takeovers and financial theft. AdaptiveMobile Security, in their technical documentation on SS7 security, specifically highlights numerous “high-profile cases of SS7 Fraud” that have received media attention. These real-world examples convinced me that SMS security risks are not just theoretical but represent real threats to personal privacy and financial security.
According to telecommunications security experts at AdaptiveMobile Security, attacks targeting SMS-based communication occur with “High” frequency on a monthly basis, demonstrating the urgent need to adopt more secure alternatives.
My Personal Security Practice Beyond Messaging
Securing my communications has been part of a broader personal security overhaul. I’ve found these complementary practices helpful:
- Using a password manager for unique credentials across services
- Enabling non-SMS two-factor authentication where available
- Regularly reviewing connected apps and services
- Being cautious about linking my phone number to new accounts
- Considering a dedicated phone number for authentication purposes
These practices work synergistically to create significantly stronger overall digital security.
Eliminating SMS security risks by switching to app-based authentication reduced successful account compromise attempts by 97% in controlled penetration tests.
Technical Attack Vectors: A Deep Dive
To fully understand the scope of the problem, it’s necessary to analyze the specific attack vectors:
1. Advanced SS7 Attacks
The vulnerabilities of the SS7 protocol allow for several types of sophisticated attacks:
MAP Location Tracking Through the MAP (Mobile Application Part) functions of SS7, an attacker with access to the SS7 network can send SendRoutingInfoForSM (SRI-SM) messages that return the user’s current location (MSC and cell). This allows:
- Precise real-time geographic tracking
- Identification of movement patterns
- Correlation with other identifiers
Interception Through CAMEL
The CAMEL (Customized Applications for Mobile Enhanced Logic) protocol can be exploited to silently duplicate SMS messages to a number controlled by the attacker.
2. IMSI Catcher and False Base Station
Physical attacks based on IMSI catchers (“Stingrays” or “cell-site simulators”) can actively intercept SMS messages:
- The device presents itself as a legitimate BTS
- Phones in the area connect automatically
- The IMSI catcher can:
- Force a downgrade to weaker encryption (A5/0 or A5/2)
- Act as a man-in-the-middle
- Decrypt traffic in real-time
These devices are now accessible for less than $1,500 with SDR (Software Defined Radio) hardware and open-source implementations.
3. Advanced SIM Swapping
SIM swapping combines social engineering and technical exploitation:
Attacks on Telephone Operators
- Exploitation of vulnerabilities in self-service portals
- Automated scripts for unauthorized port-out attempts
- Manipulation of IVR (Interactive Voice Response) systems
NIST SIM Attack Chain According to NIST, a complete attack follows this chain:
- Intelligence gathering
- Credential acquisition (data breach, phishing, social engineering)
- Impersonation
- Escalation (if necessary)
- Verification (bypassing security questions with OSINT)
- Activation (new SIM)
- Exploitation (using the number to bypass 2FA)
This can be executed in less than 30 minutes.
4. SS7 Message Modification
More advanced attacks include active message modification.
This allows:
- Inserting fake messages
- Modifying legitimate SMS messages (e.g., OTP codes)
- Impersonating trusted senders
Technical Statistics on Vulnerability
Vulnerabilities are not theoretical:
- SIM swapping attacks increased by 43% (X-Force Threat Intelligence 2024)
- 100% of tested operators (20 global) have exploitable SS7 vulnerabilities
- The effectiveness of interception attacks is estimated at 94% with SS7 access
- The average detection time for an SS7 attack is 215 hours
Multi-Factor Authentication: Superior Alternatives
TOTP (Time-Based One-Time Password)
TOTP algorithms are a superior alternative:
TOTP = HMAC(K, floor(currentUnixTime / timeStep))Where:
- K is a shared secret key
- timeStep is typically 30 seconds
- HMAC uses SHA-1 or SHA-256
- The output is truncated to 6-8 digits
Advantages:
- Offline generation
- Isolation from the risk of phone number compromise
- Resistance to passive Man-in-the-Middle attacks
WebAuthn/FIDO2
WebAuthn uses public-key cryptography with hardware secure elements:
- Registration generates an asymmetric key pair
- The private key never leaves the device
- The public key is registered with the service
- Authentication requires a signature that only the device can generate
This eliminates:
- Transmission of shared secrets
- Phishing (thanks to origin authentication)
- Impact of compromising other factors
Implementing the Migration
A complete migration requires:
Phase 1: Risk Segmentation
- Identify and prioritize critical services using SMS
- Implement secure alternatives for these services
- Assess the impact for legacy services
Phase 2: Implement Secure Protocols
- Deploy E2EE clients
- Configure secure key backups (offline)
- Verify identities (fingerprints or QR codes)
Phase 3: Harden Accounts
- Migrate 2FA from SMS to TOTP or WebAuthn
- Implement additional PINs
- Decouple the number as an identifier
Conclusion: The Imperative to Abandon SMS
Abandoning SMS hasn’t happened overnight, but it’s been one of the most significant improvements to my digital privacy. The combination of increased security, enhanced features, and peace of mind has made this transition absolutely worthwhile.
If you take nothing else from my experience, remember this: the SMS security risks for both regular messaging and 2FA are substantial, and your communications deserve protection. Modern tools make this protection more accessible than ever before. Start with a single secure chat app, convince your closest contacts to join you, and begin building a more private communication network, one conversation at a time.
The journey toward digital privacy isn’t about achieving perfection, but about making significant improvements where it matters most. Addressing SMS security risks by switching to encrypted messaging and authentication represents the perfect starting point because it affects so much of our daily digital lives. The fundamental technical vulnerabilities in the SMS protocol and the SS7 infrastructure are unresolvable with patches. The transition to E2EE communication protocols and authentication systems based on asymmetric cryptography is the only technically valid solution.
Which secure messaging app will you try first? The most important step is simply to begin.
Technical Glossary:
- SS7: Signaling System No. 7, signaling protocol for telephone networks
- IMSI: International Mobile Subscriber Identity
- TMTO: Time-Memory Trade-Off, cryptanalysis technique
- E2EE: End-to-End Encryption
- MSC: Mobile Switching Center
- SMSC: Short Message Service Center
- BTS: Base Transceiver Station
- MAP: Mobile Application Part, component of the SS7 protocol
- CAMEL: Customized Applications for Mobile Enhanced Logic
- SDCCH: Stand-alone Dedicated Control Channel
- TOTP: Time-Based One-Time Password
- WebAuthn: Web Authentication, standard for strong authentication on the web
- SMS: Short Message Service
- RCS: Rich Communication Services
- SIM: Subscriber Identity Module
Enjoyed this article? Unlock all exclusive content
Join our community for premium content. Takes just 1 minute. No spam, ever.




Leave a Reply